Tor vs VPN: What’s the Best for Online Privacy?

With increasing concerns about online privacy and security, many internet users are turning to Tor and VPNs to protect their personal information from prying eyes. Each of these tools offers a unique set of features that aim to enhance online privacy and security.
However, the question remains: which one provides the best protection for online privacy and security? In this article, we will explore the differences between Tor and VPNs and help you make an informed decision about which one is right for you.
By the end of this article, you’ll have a clear understanding of Tor and VPNs, their advantages and disadvantages, and which one is the best choice for you in terms of online privacy and security.
Understanding Tor
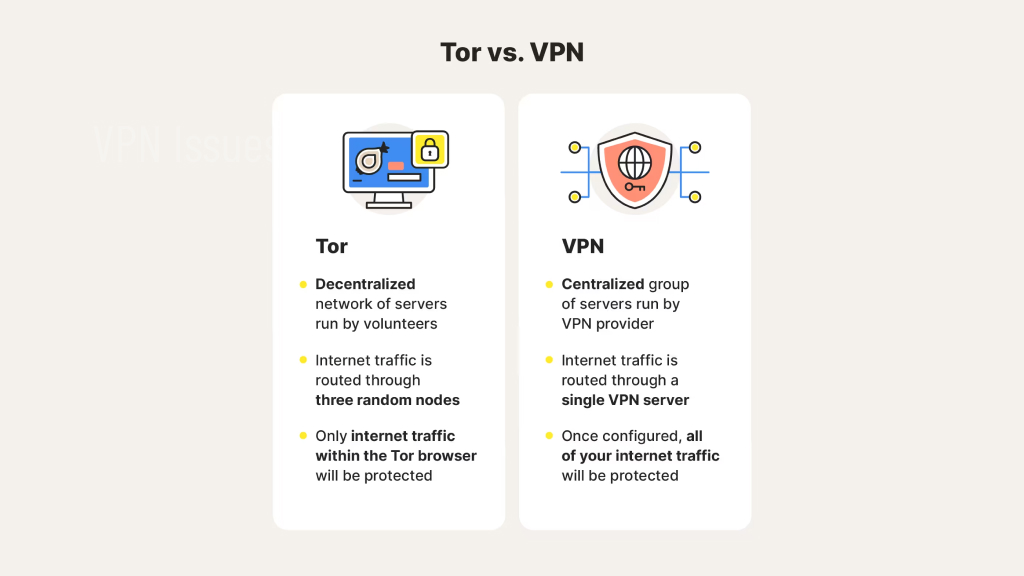
Tor is a free and open-source software that enhances online privacy and anonymity by encrypting internet traffic and routing it through a series of servers called “nodes.” Tor stands for The Onion Router, and its functionality is based on the concept of onion routing, where each layer of encryption is peeled back as the traffic passes through each node, thus obscuring the original source of the data.
One of the key advantages of Tor is its ability to protect users’ privacy and anonymity by preventing websites and servers from tracking their online activities. The encrypted traffic is also designed to prevent anyone from intercepting or analyzing the data to access sensitive information.
Tor is also particularly useful in countries with high levels of internet censorship, as it can bypass restrictions and provide access to blocked content. The software has been used by journalists, activists, and whistleblowers to protect their anonymity and safely share sensitive information.
However, as with any tool, Tor has some limitations and potential downsides. The multi-step encryption process can sometimes slow down internet speeds, and there is the possibility of running into malicious actors who operate nodes to track and monitor traffic.
| Advantages | Disadvantages |
|---|---|
| Protects online privacy and anonymity | Potential speed issues |
| Prevents website and server tracking | Possible vulnerabilities due to node operators |
| Bypasses internet censorship |
In summary, Tor is a powerful tool for enhancing online privacy and anonymity, particularly in locations with high levels of internet censorship. However, users must be aware of its potential limitations, including potential speed issues and vulnerabilities associated with node operators.
Advantages and Disadvantages of Tor
Using Tor for online privacy has many advantages and disadvantages. Some of the benefits of using Tor include anonymous browsing and access to restricted content. Tor uses encryption to protect user data and ensures that their browsing history can’t be tracked. It also allows users to access websites without revealing their physical location or IP address, which can come in handy when bypassing internet censorship.
However, using Tor also comes with some limitations. Firstly, Tor browsing can be slow due to the multiple nodes it has to use to encrypt data. Secondly, it can be vulnerable to cyber attacks and malware injections. Thirdly, Tor’s association with dark web marketplaces and illegal activities often raises red flags for law enforcement, potentially making users susceptible to monitoring by government agencies.
| Advantages | Disadvantages |
|---|---|
| Anonymous browsing | Slower browsing speeds |
| Access to restricted content | Vulnerability to attacks |
| Encryption to protect user data | Red flags for law enforcement |
Despite its limitations, Tor remains a powerful tool for enhancing online privacy and anonymity. However, users should weigh the pros and cons carefully before deciding to use it. In some cases, a VPN may be a better option, especially for users who prioritize speed and access to geo-restricted content over anonymity. Ultimately, the decision depends on the user’s specific needs and requirements.
Exploring VPN
Virtual Private Networks, or VPNs, provide a secure and encrypted tunnel between your device and the internet. VPNs offer online privacy by hiding your IP address, masking your identity and online activity from prying eyes. When you connect to a VPN, your internet traffic is routed through the VPN server, making it difficult for anyone to intercept or track your online activity, even your ISP.
VPNs employ various encryption protocols such as OpenVPN, IKEv2, or L2TP/IPSec to secure communication. Apart from encryption, VPNs also provide additional security features such as split tunneling, which allows users to route only selected traffic through their VPN connection, avoiding bandwidth problems and ensuring optimized performance.
One significant benefit of using a VPN is the ability to bypass geo-restrictions and access content that may be blocked or censored in your region. By connecting to a VPN server in a different country, you can appear as if you are physically located within that country and access restricted content.
| Pros of Using a VPN | Cons of Using a VPN |
|---|---|
| Enhanced security and privacy | May experience slow connection speeds |
| Ability to bypass geo-restrictions and access content from around the world | Some VPNs may keep records of user activity |
| Additional security features such as split tunneling | May require technical knowledge to set up and configure correctly |
Encryption Methods
VPNs use different encryption methods to secure your data. Some of the most common encryption methods include:
- OpenVPN: An open-source protocol that provides robust encryption and is highly configurable.
- IKEv2: A newer protocol that offers excellent security and stability on mobile devices.
- L2TP/IPSec: An older protocol that provides a good level of security but can be slower than other protocols.
Overall, VPNs provide a secure and private browsing experience that helps protect your online activity from hackers, government surveillance, and other prying eyes. However, not all VPNs are created equal, and it’s essential to choose a trusted provider that prioritizes privacy and security to ensure the best possible experience.
Pros and Cons of VPN
Virtual Private Networks (VPNs) have become increasingly popular in recent years as a means of enhancing online privacy and security. Here are some of the advantages and disadvantages of using a VPN:
| Pros | Cons |
|---|---|
| Encrypted connections provide an additional layer of security, making it harder for hackers to intercept your data | VPNs can sometimes cause a decrease in internet speed due to the encryption and rerouting of traffic |
| VPNs can be used to access geo-restricted content, such as streaming services that may be unavailable in certain regions | VPNs require a trusted provider, as some may not be entirely secure or may track user activity |
| VPNs can help to hide your online activity from your Internet Service Provider (ISP), preventing them from tracking and selling your data | VPNs may not be effective against more sophisticated tracking and monitoring techniques used by determined adversaries |
Overall, a VPN can be a useful tool in enhancing online privacy and security, but it is important to consider both the advantages and disadvantages before deciding whether it is right for you and your needs.
Tor vs VPN: Which One Should You Choose?
When it comes to online privacy and security, both Tor and VPN are viable options to consider. However, choosing between the two can be overwhelming, especially when you are not familiar with their differences and features. In this section, we will compare Tor and VPN head-to-head to help you make an informed decision.
Anonymity
One of the primary reasons why individuals choose Tor is its anonymous nature. Tor uses a network of multiple nodes to encrypt the user’s data, making it difficult for anyone to trace the online activities of the user. On the other hand, VPN offers partial anonymity as it uses a single server to encrypt data. Therefore, if the VPN server is compromised, the user’s online activities can be traced.
Security
Both Tor and VPN offer high levels of security, but Tor takes the lead when it comes to protecting users’ data from prying eyes. Tor encrypts data multiple times, making it nearly impossible for anyone to access it. VPN, on the other hand, uses single encryption, which is susceptible to hacking and data breaches.
Overall effectiveness
In terms of effectiveness, VPN leads the way, especially in terms of speed. Tor’s multi-encryption slows down the data transfer, making it slower than the VPN connection. VPN allows you to bypass censorship, access geo-blocked content, and stream HD videos without buffering, features that are not possible with Tor due to its slower speeds.
Ultimately, the choice between Tor and VPN depends on your specific needs. If you require maximum anonymity and don’t mind the slower speeds, Tor should be your choice. If you prioritize speed and want to access geo-restricted content, VPN is the way to go. Regardless of which one you choose, both Tor and VPN will provide enhanced online privacy and security.
Conclusion
Choosing between Tor and VPN ultimately comes down to personal preference and your specific online privacy and security needs. Both options provide strong encryption and offer varying degrees of anonymity.
If you prioritize maximum anonymity and don’t mind potentially slower speeds, Tor may be the better choice. However, for those who prioritize faster speeds and want to access geo-restricted content, VPNs are a great option.
It’s also important to consider the potential downsides of each option. Tor can be vulnerable to attacks and may not be the best choice for activities that require absolute anonymity. On the other hand, VPNs require a trusted provider and may not be foolproof against determined hackers.
Overall, Tor and VPN are both viable choices for enhancing online privacy and security. Consider your priorities and needs carefully before making a decision between the two.
Remember, whether you choose Tor, VPN, or another privacy-enhancing tool, it’s important to prioritize online privacy and security in today’s digital age.
Thank you for reading this article on Tor vs VPN and online privacy and security. We hope you found it informative and helpful in making an informed decision. Stay safe and secure online!
FAQ
What is the difference between Tor and VPN?
Tor and VPN are both tools used for enhancing online privacy and security, but they work in different ways. Tor is a network of volunteer-operated servers that encrypts and routes internet traffic through multiple relays, making it difficult to trace the user’s identity. On the other hand, a VPN creates a secure, encrypted connection between the user’s device and a remote server, masking their IP address and encrypting all data transmitted. While Tor focuses on anonymity and bypassing internet censorship, VPNs offer encryption and secure browsing.
Is Tor more secure than a VPN?
Tor and VPNs provide different types of security. Tor provides anonymity by bouncing your internet traffic through multiple relays, making it difficult to trace back to your device. However, this doesn’t guarantee complete security as there may be vulnerabilities in the Tor network itself. VPNs, on the other hand, provide encryption and secure connections, making it virtually impossible for anyone to intercept your data. Ultimately, the level of security you need depends on your specific requirements and threat model.
Can Tor and VPN be used together?
Yes, Tor and VPNs can be used together to further enhance your online privacy and security. This setup is known as “Tor over VPN” or “VPN over Tor.” When using Tor over VPN, your internet traffic is first routed through a VPN server, and then through the Tor network. This adds an extra layer of encryption and anonymity. However, it’s important to choose a VPN provider that supports this configuration. It’s worth noting that using Tor over VPN may impact your internet speed due to the additional routing.
Which option is better for bypassing internet censorship: Tor or VPN?
Tor is known for its effectiveness in bypassing internet censorship due to its decentralized network and multiple relays. It allows users to access blocked websites by routing their traffic through different countries. However, in some cases, authorities may block access to known Tor entry or exit nodes, which can limit its effectiveness. VPNs can also bypass censorship by routing your traffic through servers located in countries with more lenient internet policies. Therefore, both Tor and VPNs can be useful tools in circumventing censorship, but their effectiveness may vary depending on the specific situation.
Do Tor and VPN guarantee complete anonymity?
While Tor and VPNs can enhance your anonymity and privacy online, it’s important to understand that no tool can provide 100% anonymity. Tor does a good job of hiding your real IP address and encrypting your traffic, but it has its limitations. If an attacker controls a significant number of relays, they may be able to deanonymize users. Similarly, VPNs can protect your data and mask your IP address, but they are only as secure as the VPN provider and the encryption protocols they use. It’s crucial to use reliable tools and follow best practices to maximize anonymity.