What is Encryption? Unlocking the Basics

Welcome to our comprehensive guide on encryption! In this article, we will delve into the world of encryption and help demystify its importance in securing data. Whether you’re a tech enthusiast or simply curious about digital privacy, understanding encryption is essential in today’s interconnected world.
So, what exactly is encryption? Encryption is a process of converting plain, readable data into an encoded form, making it unreadable to unauthorized individuals. By using complex mathematical algorithms, encryption transforms your sensitive information into a secure code, ensuring that only authorized parties can decipher it.
There are various types of encryption that serve different purposes. The most commonly used encryption methods include symmetric encryption and asymmetric encryption. Symmetric encryption relies on a single encryption key to both encrypt and decrypt data, while asymmetric encryption involves a pair of keys – a public key for encryption and a private key for decryption.
Encryption keys and algorithms are the driving forces behind the encryption process. An encryption key is a unique sequence of characters that determines how the data is scrambled and unscrambled. Encryption algorithms, on the other hand, are intricate mathematical processes that manipulate the data using the encryption keys.
Why is data encryption crucial? In today’s digital landscape, protecting sensitive information is paramount. Data encryption acts as a powerful shield against cyber threats and potential breaches. By encrypting your data, you add an extra layer of security, ensuring that even if your information falls into the wrong hands, it remains unreadable and unusable.
Throughout this article, we will explore encryption in depth, covering the different types, the role of encryption keys and algorithms, and the significance of data encryption. By the end of this guide, you will have a solid understanding of encryption basics and be equipped to make informed decisions to safeguard your personal and business data.
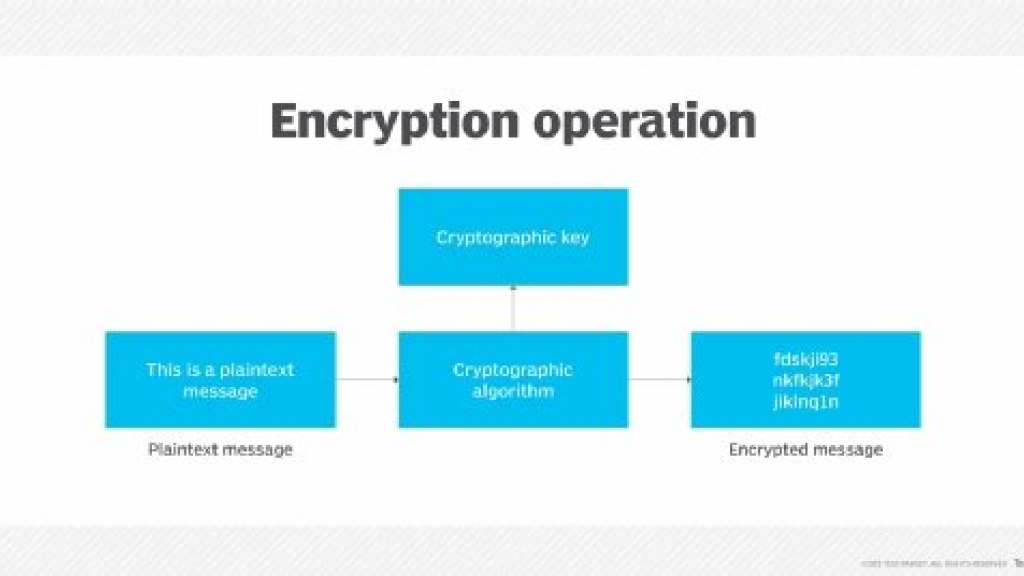
Understanding Encryption: Definition and Types
In this section, we will delve deeper into the concept of encryption and explore its definition and various types. Encryption is a fundamental technique used to secure information by converting it into an unreadable format, known as ciphertext. By doing so, encryption protects data from unauthorized access and ensures its confidentiality.
There are two primary types of encryption: symmetric encryption and asymmetric encryption.
Symmetric Encryption
Symmetric encryption, also known as secret-key encryption, involves the use of a single key for both encryption and decryption. This key is shared between the sender and the recipient, providing them with the ability to encrypt and decrypt messages or files securely.
One of the most commonly used symmetric encryption algorithms is the Advanced Encryption Standard (AES). AES uses different key sizes, such as 128-bit, 192-bit, or 256-bit, to provide varying levels of security.
Asymmetric Encryption
Asymmetric encryption, also known as public-key encryption, uses a pair of keys – a public key and a private key. These keys are mathematically related, but distinct from one another.
The public key is freely shared, allowing anyone to encrypt data. However, only the corresponding private key held by the intended recipient can decrypt the encrypted data, ensuring confidentiality.
One of the most commonly used asymmetric encryption algorithms is the Rivest-Shamir-Adleman (RSA) algorithm. RSA is widely used in digital signatures and secure communication protocols.
Table: Comparison of Symmetric and Asymmetric Encryption
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Management | Requires secure distribution of the shared key | Public and private key pairs |
| Speed | Fast encryption and decryption | Slower than symmetric encryption |
| Use Cases | Data encryption, VPN tunnels | Digital signatures, secure communication |
| Key Length | Smaller key length | Larger key length |
| Security | Relies on key management and secrecy | Provides stronger security due to separate keys |
By understanding the definition and types of encryption, readers will gain insights into how encryption works and its role in protecting sensitive information. In the next section, we will explore encryption keys and algorithms in further detail.
Exploring Encryption Key and Algorithms
In the world of encryption, two fundamental components play a crucial role in securing data: encryption keys and algorithms. Understanding how these elements function is essential to grasp the technical aspects of encryption and its underlying mechanisms.
Encryption Keys: Securing Information
An encryption key is a unique string of characters that is used to lock and unlock encrypted data. It acts as a critical element in the encryption process, determining the transformation of plain text into unreadable ciphertext and vice versa. Without the correct encryption key, the data remains inaccessible, ensuring its security even if intercepted.
Encryption keys come in various lengths and complexities, and their strength directly affects the level of security offered. Longer keys with a higher degree of randomness are more resistant to brute force attacks, making it harder for unauthorized individuals to decipher the encrypted data.
Furthermore, encryption keys can be classified into two types: symmetric and asymmetric encryption keys.
- Symmetric Encryption Keys: Also known as secret keys, these encryption keys use the same secret key for both the encryption and decryption processes. This means that both the sender and the receiver must possess the same key, making secure key distribution a crucial consideration. Symmetric encryption is highly efficient and typically used for large amounts of data.
- Asymmetric Encryption Keys: Also referred to as public/private key pairs, these encryption keys utilize a combination of a public key and a private key. The public key is used for encryption, while the private key is kept secret and used for decryption. Asymmetric encryption provides secure key exchange in scenarios where the sender wants to share sensitive information with multiple recipients.
Encryption Algorithms: Enhancing Security
Encryption algorithms are mathematical processes that encrypt and decrypt data using encryption keys. These algorithms determine the complexity, strength, and level of security provided by an encryption system.
There are various encryption algorithms available, each with its own unique characteristics and strengths. Some commonly used encryption algorithms include:
- AES (Advanced Encryption Standard): A widely adopted symmetric encryption algorithm renowned for its high level of security and efficiency.
- RSA (Rivest-Shamir-Adleman): A popular asymmetric encryption algorithm that uses the mathematics of prime numbers for secure key exchange.
- DES (Data Encryption Standard): Although it is no longer considered secure for sensitive data, DES was once widely used as a symmetric encryption algorithm.
The choice of encryption algorithm depends on several factors, including the desired level of security, computational efficiency, and compatibility with existing systems.
By understanding encryption keys and algorithms, individuals and organizations can make informed decisions when it comes to securing their sensitive data. These vital components work in harmony to ensure the confidentiality and integrity of information, safeguarding digital privacy.
Data Encryption: Protecting Information
In today’s digital landscape, data encryption plays a crucial role in safeguarding sensitive information. With the ever-increasing risks and threats in cyberspace, it is imperative to implement robust encryption measures to protect personal and business data.
Encryption provides a protective shield against unauthorized access, ensuring that only authorized individuals can decipher and access encrypted data. By converting plaintext into ciphertext, data encryption renders information unreadable and indecipherable to unauthorized parties.
Implementing data encryption measures helps prevent data breaches, identity theft, and unauthorized surveillance. It enhances confidentiality and privacy, providing individuals and organizations with peace of mind that their sensitive data remains secure.
Whether it’s financial information, customer data, intellectual property, or confidential emails, data encryption is a powerful tool to combat potential security breaches. By implementing strong encryption protocols and using robust encryption algorithms, individuals and businesses can fortify their data against cyber threats.
Data encryption also enables compliance with data protection regulations such as the General Data Protection Regulation (GDPR) and other industry-specific standards. Encrypting data not only safeguards information but also helps to meet legal requirements and avoid hefty penalties for non-compliance.
Ultimately, data encryption serves as an essential safeguard for digital privacy and protection. By integrating encryption into our digital infrastructure, we can defend against evolving cyber threats and preserve the confidentiality and integrity of our valuable data.
Symmetric vs. Asymmetric Encryption: A Closer Look
Encryption plays a vital role in protecting sensitive information and ensuring data security. In this section, we will compare two common encryption methods: symmetric encryption and asymmetric encryption. By understanding the advantages and disadvantages of each approach, you will gain insights into their respective use cases and the best practices for implementing them.
Symmetric Encryption
Symmetric encryption, also known as secret key encryption, uses the same key for both the encryption and decryption processes. This method is faster and more efficient than asymmetric encryption, making it ideal for securing large volumes of data.
In symmetric encryption, it is crucial to protect the encryption key since it holds the power to unlock the encrypted data. If the key falls into the wrong hands, all the encrypted information becomes vulnerable. This key distribution challenge restricts symmetric encryption’s use case to secure communication between parties who already have a shared secret key.
Asymmetric Encryption
Asymmetric encryption, also called public-key cryptography, uses a pair of keys: a public key for encryption and a private key for decryption. The public key is widely shared, allowing anyone to access it, while the private key is kept confidential by the key owner.
With asymmetric encryption, secure communication can be established between parties who have never communicated before. The sender encrypts the message using the recipient’s public key, and only the recipient, possessing the corresponding private key, can decrypt and access the information.
Although asymmetric encryption ensures secure communication between unknown parties, it is computationally intensive and slower than symmetric encryption. Due to its computational overhead, asymmetric encryption is commonly used for tasks such as securely exchanging symmetric keys for subsequent communication.
| Features | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Speed and Efficiency | Fast and efficient | Computationally intensive and slower |
| Key Distribution | Requires a shared secret key | No prior communication required |
| Use Cases | Large volume data encryption | Secure communication with unknown parties |
Encryption Software and Techniques
In this section, we will delve into the world of encryption software and techniques that are commonly used to implement encryption protocols. Encryption plays a crucial role in ensuring the confidentiality and integrity of data, and the right combination of software and techniques can greatly enhance data security.
When it comes to encryption software, there are various solutions available in the market that cater to different needs and requirements. These software solutions employ encryption algorithms to transform plain text into cipher text, making it unreadable to unauthorized users. Some popular encryption software options include:
- BitLocker: Developed by Microsoft, BitLocker offers full disk encryption for Windows operating systems. It provides a seamless and transparent encryption experience, protecting data at rest.
- FileVault: Exclusive to macOS, FileVault provides native encryption capabilities for protecting files and folders. It utilizes the user’s login password as an encryption key.
- VeraCrypt: An open-source encryption software, VeraCrypt offers cross-platform compatibility and supports various encryption algorithms. It provides flexible options for creating encrypted volumes and containers.
In addition to encryption software, there are several techniques that can enhance data security and privacy. These techniques can be applied in conjunction with encryption algorithms to strengthen the overall encryption process. Some common encryption techniques include:
- Hashing: Hash functions generate fixed-size, unique hashes for input data. These hashes are used to verify data integrity and detect any unauthorized modifications.
- Salting: Salting is the process of adding additional random data to a plain text before encryption. This technique adds complexity to the encryption process, making it more resistant to brute force attacks.
- Key Management: Effective key management is crucial for maintaining the security of encryption systems. It involves securely generating, storing, and distributing encryption keys.
By utilizing the right encryption software and techniques, individuals and organizations can ensure that their data remains secure and confidential. The table below provides a comprehensive overview of the popular encryption software options mentioned above:
| Encryption Software | Description |
|---|---|
| BitLocker | Microsoft’s full disk encryption software for Windows operating systems. |
| FileVault | macOS native encryption software for protecting files and folders. |
| VeraCrypt | Open-source encryption software with cross-platform compatibility. |
Conclusion
Throughout this article, we have explored the fundamentals of encryption and its vital role in securing data and maintaining privacy in the digital age. Encryption, defined as the process of converting information into an unreadable format, provides a powerful shield against unauthorized access and potential threats. By employing encryption techniques, individuals and businesses can safeguard sensitive information and ensure the confidentiality and integrity of their data.
We have discussed the different types of encryption, including symmetric and asymmetric encryption, and highlighted their respective strengths and weaknesses. Understanding the distinctions between these approaches allows for informed decision-making regarding the implementation of encryption protocols.
Data encryption has emerged as a crucial measure to protect information in an increasingly interconnected world. By encrypting sensitive data, individuals and organizations can mitigate the risk of data breaches, identity theft, and other cyber threats. Encryption not only serves as a defense mechanism but also helps maintain privacy and compliance with data protection regulations.
In conclusion, encryption serves as an essential pillar of digital security, enabling the safe transmission and storage of valuable information. By implementing encryption measures and staying informed about evolving encryption technologies, individuals and businesses can reinforce their data protection strategies and contribute to a safer online environment.
FAQ
What is encryption?
Encryption is the process of converting data or information into a form that is unreadable to unauthorized users. It ensures that only authorized individuals who possess the decryption key can access and understand the encrypted data.
What are the different types of encryption?
There are two main types of encryption: symmetric encryption and asymmetric encryption. Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption uses a pair of keys – a public key for encryption and a private key for decryption.
How do encryption keys and algorithms work?
Encryption keys are used to scramble and unscramble data during encryption and decryption processes. They are generated using algorithms, which are mathematical instructions used to transform data. The strength of an encryption algorithm determines the level of security it provides for encrypted data.
Why is data encryption crucial for digital privacy and protection?
Data encryption is critical for digital privacy and protection because it ensures that sensitive information remains secure and unreadable to unauthorized individuals. It helps safeguard personal and business data from unauthorized access, data breaches, and cyber attacks.
What are the differences between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, making it faster but requiring secure key distribution. Asymmetric encryption uses a pair of keys, making it secure for communication but slower due to complex mathematics involved.
What are some popular encryption software solutions and techniques?
Popular encryption software solutions include BitLocker, VeraCrypt, and FileVault for disk encryption, and OpenVPN and IPsec for network encryption. Encryption techniques such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) are widely used to enhance data security.